DukenukemX
Supreme [H]ardness
- Joined
- Jan 30, 2005
- Messages
- 7,953
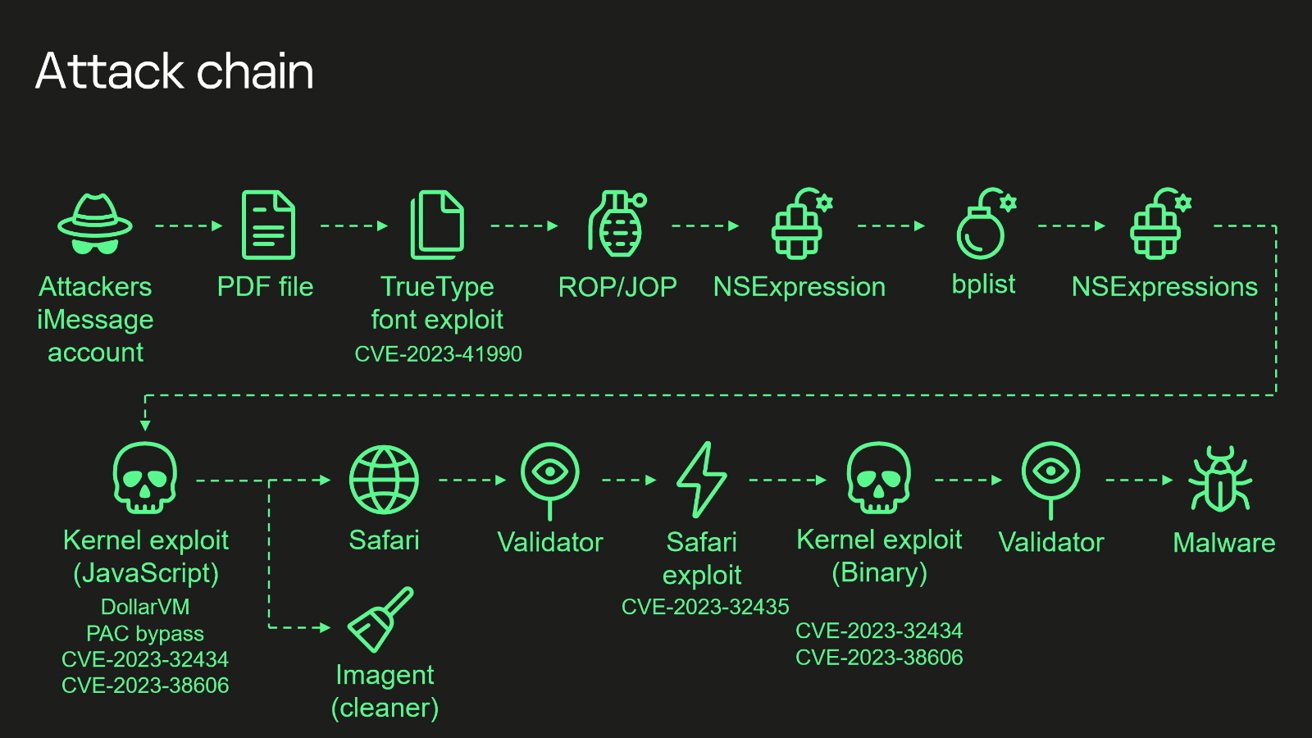
I've read it called zero-click but I'm not sure if they're referring to this. What's interesting is that this is done through iMessage which was already shown to have vulnerabilities through Beeper. What's also interesting is that this attack used hardware that nobody knew about in iPhones. All Apple can do is block access to parts of the memory.No click required.
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)