alright, pertinent details
(ips changed blah blah)
main network is 192.168.1.0/24
increasing wifi coverage, need to setup DHCP(no dhcp currently, dont ask, not my call)
would like to do this on 192.168.2.0/24
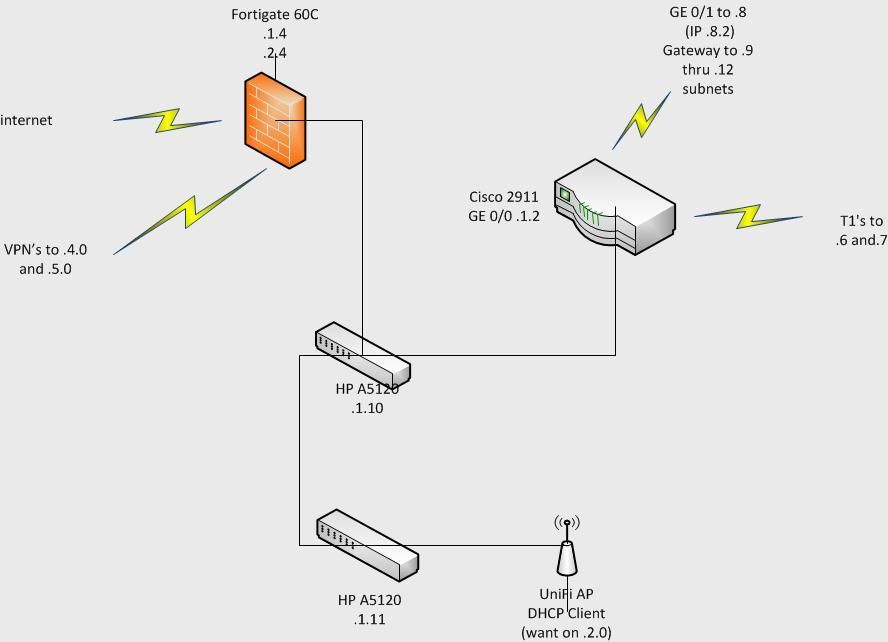
I have a cisco 2911 at .1.2
and a fortigate 60c at 1.4
the 60c sits between the network, and the internet doing its job as a UTM and handling a few P2P vpn's, the cisco has some T1's to other offices into it
I gave the fortigate a secondary IP of .2.4 and set a DHCP pool on the internal interface to hand out .2.100-.2.150
it will not work. the 2911 has a 0.0.0.0/0.0.0.0 route that points to the 60C, I added a route in for 232.0 on it to point at .1.4 as a test and it did not help.
the 60c and 2911 are not directly connected, but both go to the same switch
the device that I am trying to get DHCP is attached to a different switch, which is on a 10gb link to the other one. if I put DHCP on .1.0 it works just fine so its not the 60cs dhcp server just not working.
I am just missing something. and I am not sure what
its making me feel very silly. if it was easier to do so I would just give all my .1 stuff a subnet of .254.0 but since its about 150 devices on static ip's thats a huge undertaking I am trying to avoid(and I think that would fix the issue?)
(ips changed blah blah)
main network is 192.168.1.0/24
increasing wifi coverage, need to setup DHCP(no dhcp currently, dont ask, not my call)
would like to do this on 192.168.2.0/24
I have a cisco 2911 at .1.2
and a fortigate 60c at 1.4
the 60c sits between the network, and the internet doing its job as a UTM and handling a few P2P vpn's, the cisco has some T1's to other offices into it
I gave the fortigate a secondary IP of .2.4 and set a DHCP pool on the internal interface to hand out .2.100-.2.150
it will not work. the 2911 has a 0.0.0.0/0.0.0.0 route that points to the 60C, I added a route in for 232.0 on it to point at .1.4 as a test and it did not help.
the 60c and 2911 are not directly connected, but both go to the same switch
the device that I am trying to get DHCP is attached to a different switch, which is on a 10gb link to the other one. if I put DHCP on .1.0 it works just fine so its not the 60cs dhcp server just not working.
I am just missing something. and I am not sure what
its making me feel very silly. if it was easier to do so I would just give all my .1 stuff a subnet of .254.0 but since its about 150 devices on static ip's thats a huge undertaking I am trying to avoid(and I think that would fix the issue?)
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)